
As an Approved Scanning Vendor (ASV), CampusGuard and the RedLens InfoSec team can perform your required external vulnerability scans for PCI.
The CampusGuard vulnerability scanning service scans networks, systems, and software from an attacker’s point of view. We use industry-standard automated and manual scanning tools that have been well-tested to discover vulnerabilities, such as deficiencies in patch management, the use of weak protocols or services, and misconfigurations that could lead to information leakage. These tools contain vast libraries of checks to ensure that present vulnerabilities are appropriately identified.
You will want to confirm with your CRM if scanning is already part of your Annual Support Agreement. If scanning is not included within your current contract terms, your CRM can provide more details on how we can perform these services.
Scan Request
When you are ready to start scanning a system or systems, you can use the tools within the CampusGuard Central® portal to request a new, recurring cardholder data environment (CDE) scan. From your PCI Dashboard:
- Click the “Scans” button at the top of your screen.
- You will see an option to “Schedule Scan.”
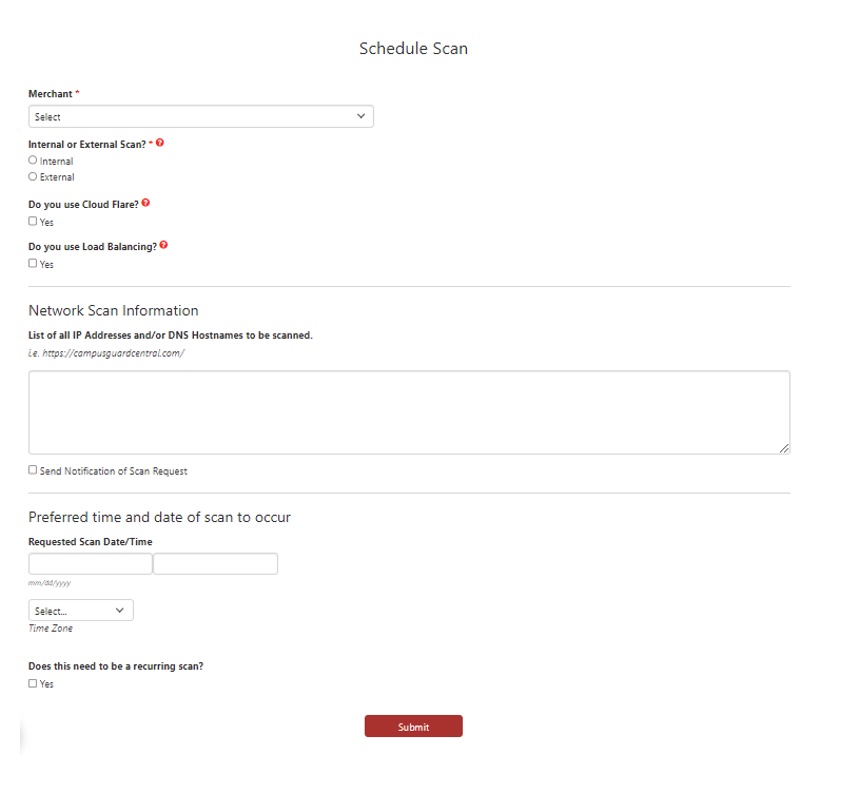
- Select the assigned Merchant area(s) that requires a scan to be run. You will most likely want to schedule one overall scan for your entire CDE, so you can work with your dedicated team to review the in-scope systems and provide a list of all included IP addresses/systems. This way, you will have one consolidated report that can be provided to your acquiring bank upon request.
- Select “Internal” or “External” Scan. External scans are scans performed by a scanner that is external to your network, or from a position that is outside of your network perimeter. Internal scans are scans that originate from a scanner that sits inside of the network perimeter.
- Select Scan Type. “Network Vulnerability” or “Web Application” scan, and if the scan is being performed to meet PCI requirements.
- Note if the scan needs to be authenticated. If the web application scan needs to be authenticated, the Operations Support team will follow up with an encrypted email to obtain the necessary credentials.
- Select “Yes” if you have Cloudflare deployed. To effectively scan systems utilizing Cloudflare services, the scan must be configured with slightly different settings to prevent scanning delays and interference. Cloudflare’s services are designed to enhance the performance, security, and reliability of websites and web applications. Some of the key features and services provided by Cloudflare include DDoS protection, load balancing, and Web Application Firewall (WAF).
- Select “Yes” if your web server uses load balancers. Web server load balancing is a technique used to distribute incoming network traffic or client requests across multiple web servers. The primary goal of load balancing is to ensure that each server in a cluster shares the workload efficiently, thereby improving the performance, availability, and scalability of a web application. Per the PCI Council’s Approved Scanning Vendor (ASV) Program Guide:
- If using localized load balancers, the ASV must obtain documented assurance from the scan customer that the infrastructure behind the load balancer(s) is synchronized in terms of configuration.
- Regardless of whether localized load balancers or external load balancing services (such as Cloudflare or Amazon Elastic Load Balancer) are being used, the configuration and the customer’s assurance must be clearly documented.
- Enter the Scan Information (the IP addresses and/or the DNS hostnames that should be scanned). When scanning through Qualys we are currently unable to scan specific directories (i.e., www.website.com/specificdirectory) and will need to scan the entire host (i.e., website.com), although this is something that may change as PCI DSS v4.0 is adapted by more organizations this year.
- Add the preferred date and time for the scan to run.
- If this should be a recurring scan (i.e., run quarterly for PCI compliance), select “Yes” and then determine how often and when you would like this scan to run each selected period.
- Click “Submit.”
- The CampusGuard team will confirm receipt of your scan request and work with you to designate the team members who should be notified each month or quarter before the scan runs and who should be notified of the scan results.
- The scans will be coming from a cloud-based scanner. The scanner should be treated as any other Internet host and no changes to your perimeter security should be made except to whitelist the scanner’s IP addresses in your IPS or active IDS (if you have one between the Internet and your host being scanned). Before scanning, CampusGuard/RedLens will provide this information.
Reporting
- Upon scan completion, an ASV staff member will review the results. The RedLens Infosec ASV team will provide both executive and technical level reports for all ASV external vulnerability scans, which include remediation instructions prioritized by severity and frequency using the Common Vulnerabilities and Exposures (CVE) rating system.
- Once the reports are uploaded to CampusGuard Central®, the RedLens team is available to help address any questions about steps for remediation, as well as talk through any possible false positives and evidence needed to note a false positive moving forward. Our qualified ASV team is very hands-on and can consult with your teams as needed.
- Once remediated, a re-scan can be requested via the CampusGuard Central® compliance portal, and an updated report will be provided.
- Each quarter, the Operations Support team will reach out to your team to confirm the IP addresses/systems included within your quarterly CDE scan. This is a requirement from the PCI Council’s ASV Program Guide, and the scan confirmation must be received before report delivery.
Within CampusGuard Central®, your PCI team will be able to track your ongoing vulnerability scans. The Scan Dashboard will show requested scans, scan type, recurrence, included IP addresses, completed reports, and scan status so you can easily oversee and track this piece of your required compliance cycle. Within the merchant dashboard, you are also able to designate which of your SAQ A merchants require scanning, so you can track and monitor whether these requirements are being met quarterly.
Please don’t hesitate to reach out to your dedicated CRM team with any questions you have about navigating CampusGuard Central® and/or how to get started with the quarterly ASV scans.
Interested in learning about CampusGuard Central®? Watch our Live Demo on demand:

