As the new year unfolds, it heralds a fresh chapter in the evolution of my penetration testing approach. In the span of the initial quarter, my assessments have yielded not only two CVEs, but also a significant discovery—a bypass in a major Web Application Firewall (WAF).
This comes on the heels of my recent blog post, “Beyond the Web Application Firewall,” where I emphasized the critical need for intrinsic security measures within the application code itself, beyond mere reliance on WAF technology. It seems almost predestined that I would encounter an AWS WAF Bypass so soon after advocating for deeper security integration.
In the ever-evolving landscape of cybersecurity, vigilance is paramount. Recently, while conducting a routine security assessment for a client’s web application, I stumbled upon a soft spot in the armor of AWS’s WAF. This discovery underscores a critical vulnerability that could potentially compromise the security of numerous applications protected under AWS’s umbrella.
The Discovery
The AWS WAF is designed to safeguard web applications by filtering and monitoring HTTP requests. However, during my examination, I unearthed a method to circumvent this protective barrier using Unicode Sequential encoding.
This technique enabled the transmission of malicious payloads directly to the server, bypassing the WAF’s defenses undetected. Numerous other payloads, which included a variety of encodings such as URL and basic ASCII, were detected by the WAF and web application itself and blocked immediately.
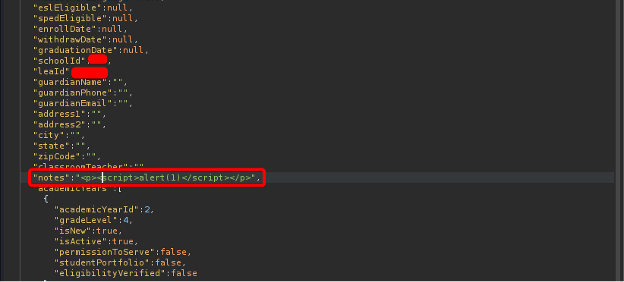
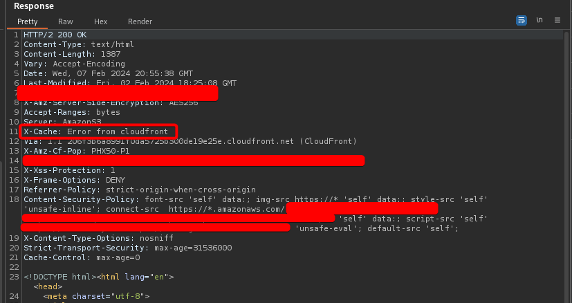
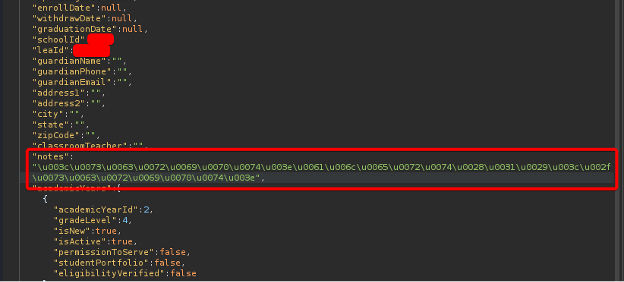
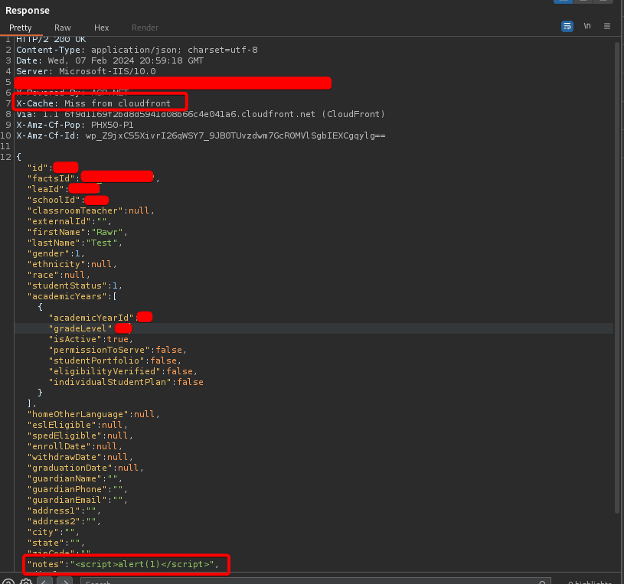
After testing Unicode Sequential encoding, however, it was found that AWS’s WAF accepted this form of payload, while the web application decoded it and stored it in its database.
The Implications
This revelation is particularly alarming as it applies not only to Cross-Site Scripting (XSS) attacks but also to a broad spectrum of malicious payloads that the WAF would typically block. The client’s configuration, which was a standard AWS WAF setup, complemented by a custom rule for file uploads, included several managed rulesets:
- AWS-AWSManagedRulesAmazonIpReputationList
- AWS-AWSManagedRulesAnonymousIpList
- AWS-AWSManagedRulesCommonRuleSet
- AWS-AWSManagedRulesKnownBadInputsRuleSet
- AWS-AWSManagedRulesSQLiRuleSet
- AWS-AWSManagedRulesWindowsRuleSet
Despite these measures, the Unicode Sequential encoding bypass persisted.
Proactive Measures
Upon identifying the issue, I promptly informed the client and recommended the implementation of additional backend security protocols, including input filtering and output encoding. Moreover, I proposed the creation of a bespoke WAF rule to detect and thwart Unicode Sequential encoding attempts.
A Call to Action
I have reached out to AWS to share these findings, as they bear significant implications for other customers relying on the WAF service. It is imperative to ascertain whether AWS is cognizant of this bypass technique and if there are plans afoot to fortify the default ruleset against such exploits. Enhancing the WAF’s security measures is crucial to safeguarding customers from potential cyber threats.
At the time of writing this article, AWS and I have been in constant communication, and they have released a patch for it.
Technical Deep Dive
For those interested in the technical specifics, the bypass was executed using a Python script that converted ASCII input into Unicode Sequential encoding. Here’s a simplified version of the script used:
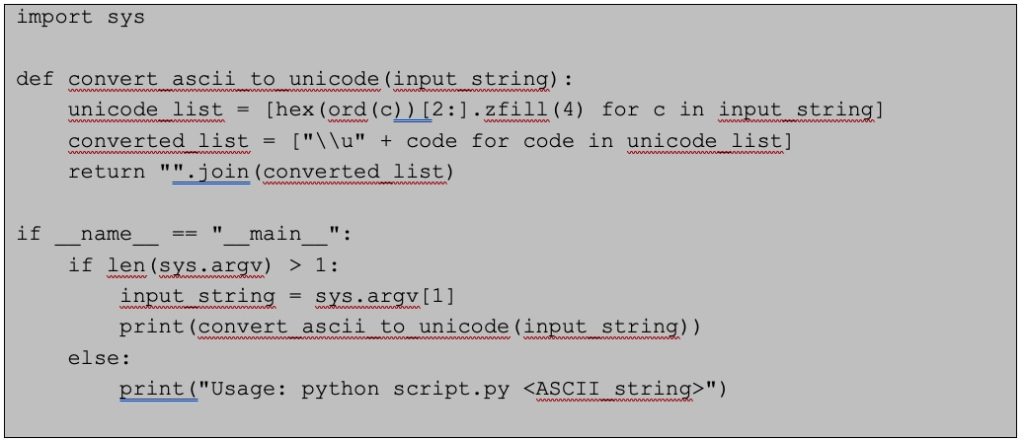
The script’s output, when deployed, resulted in the server accepting the encoded payload and decoding it back to ASCII without any HTML encoding. This flaw could have severe repercussions for companies utilizing AWS’s WAF, as it could lead to successful payload injections.
Conclusion
The cybersecurity realm is fraught with challenges, and this incident serves as a stark reminder of the constant need for innovation and adaptation. As we continue to fortify our defenses, collaboration, and transparency remain key in the collective effort to stay one step ahead of malicious actors.
RedLens InfoSec, CampusGuard’s trusted security team, is ready to collaborate with you to reduce risks and enhance your organization’s cyber defenses. Contact us today to get started.

