
Threat Intel Update
In recent weeks U.S. and international law enforcement partners have had success disrupting multiple marketplaces selling valuable personal information and login credentials, these coordinated operations demonstrate the level of cooperation needed to disrupt cyber operations and the global infrastructure and network of cyber actors. Despite these successes, other cyber actors will create new marketplaces or other existing marketplaces will see increased business activity, serving as a reminder personal data is a highly valuable resource to cyber actors, and its protection is important.
While cyber actors have monetized the sale of stolen data to other interested cyber actors, extorting victims to pay for the return of their stolen data is a growing risk, forcing the choice between paying to retrieve the data, or risk-sensitive company, client, or personal data being released on the Dark Web where it can exploit by cyber actors.
Cyber Attacks
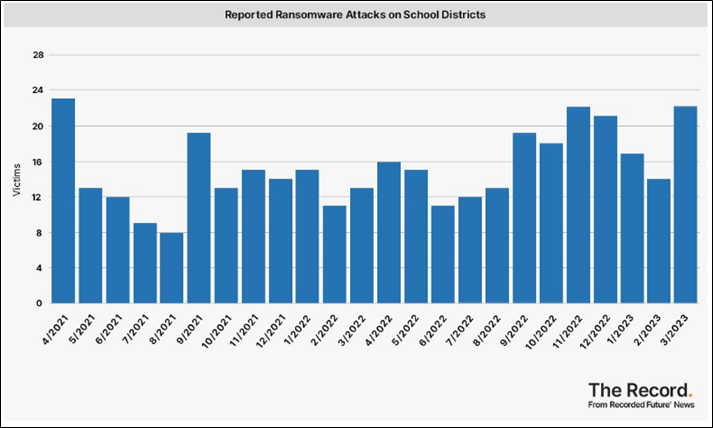
Ransomware Attacks Against Education Institutions Increased in March 2023, the Highest Number in Two Years, the total of 22 ransomware attacks matches the number of ransomware attacks in November 2022 and due to the ransomware attacks, multiple education institutions were forced to cancel classes. Additionally, the LockBit ransomware variant had the most victims posted to extortion sites as of March 2023. The Record
Computer Hardware Manufacturer, Victim of Ransomware Attack and Extorted for $4 Million for Stolen Data, MSI, a Taiwan-based company, has not indicated what type of data was taken or what systems were impacted but MSI has instructed victims to obtain firmware and BIOS updates from official sources. However, the ransomware group Money Message, has indicated it stole files from the company and is demanding a payment of $4 million or it will leak the data. Tech Radar
Clop Ransomware Actors Release 16,000 Documents for Students in Australia’s Tasmania,, the records were likely obtained from Fortra GoAnywhere file transfer product, which has a vulnerability Clop has been exploiting to obtain data from victims. The data likely includes financial invoices, student names and addresses, and information on student assistance programs. The Record
Western Digital Suffers Data Breach, Limiting Customer Access Cloud Services, on April 3rd, the company announced the company had suffered a data breach in late March and stole company data. As a result of the incident, Western Digital limited access to their My Cloud Home, My Cloud Home Duo and SanDisk ibi platforms, which impacted the ability to use mobile, desktop, and web application services. The company has been able to offer customers limited local access to some of their services and data stored by Western Digital. Cybersecurity Dive
Cyber Financial Fraud & Crime
Cyber Actors Exploit Free Accounts From Legitimate Services to Distribute Fake Invoices to Facilitate Business Email Compromise Schemes, this activity has been identified as part of a new wave of BEC attacks, enabling cyber actors to bypass email defenses in place to detect or prevent BEC attacks. Cyber actors use legitimate services to create free accounts and then send out fake invoices to victims in an effort to get the victims to call the number listed in the invoice. When victims call the number, the cyber actors can use the victims number to facilitate future cyber-attacks through mobile applications or text messages.Avanan
Chinese Cyber Actors Establish Extensive Ecosystem to Engage in Card-Not-Present Fraud Activity, an identified carding forum had over 96,000 users and could pay in Bitcoin to obtain training on how to engage in phishing campaigns to obtain credit card information and monetize the stolen card information. Chinese cyber actors establish an extensive digital infrastructure engage in phishing activity, and use compromised residential proxies to gain access to targeted websites in order to obfuscate their location and also utilized URL redirect tools to disguise phishing URLs to challenge phishing detection mechanisms. AT&T Cybersecurity
New Dark Web Market, Styx Marketplace, Focused on Facilitating Cyber Financial Crime, the market opened in January, offering credit card information, SIM cards, and forged documents for sale by paying in Tether, Ethereum, or Bitcoin. Victim data on Styx Marketplace includes victims from the U.S., U.K., Australia, Canada, and countries throughout Asia. Dark Reading
Malicious Browser Extension, Rilide, Used to Steal Cryptocurrency, the extension targets the Chrome, Brave, Opera and Edge browsers and can take screenshots of victim systems as well as inject scripts into webpages. Rilide has been distributed through Google ads and the Aurora stealer to load the malicious extension, while also being delivered to the Ekipa remote access trojan, which is distributed through a malicious macro and Rilide also has the capability to bypass two-factor authentication. Bleeping Computer
Cyber Compliance, Enforcement, & Policy
U.S. Court Approves Joint Effort by Microsoft, cybersecurity company Fortra, and the Health Information Sharing and Analysis Center to Disrupt Malicious Versions of Cobalt Strike and Microsoft Software, the three organizations are working together to prevent the use of legitimate tools being abused by cyber actors. Cobalt Strike is a legitimate tool, distributed by Fortra, and is used for penetration testing, but cracked legacy versions have been exploited to distribute various ransomware variants, including over 60 attacks in the health sector. Cyber actors have also distributed fake software updates for Microsoft products, which has provided access to victim computers used to distribute ransomware. Microsoft
Multinational Law Enforcement Effort Disrupts Genesis Market, Online Marketplace for Access Credentials, the marketplace had approximately 1.5 million stolen identities for sale. Along with the seizure of the domain disrupting its ability to operate, 119 individuals were arrested, over 200 properties were searched and 97 knock-and-talk interviews were conducted. As part of a multinational operation to disrupt the Genesis Market, the Dutch Police have created a website, which can be used to check if your personal information has been posted for sale on the Genesis Market. Europol
U.S. Law Enforcement Seizes Over $110 Million in Funds Illicitly Obtained from Cryptocurrency Investment Schemes, the funds were laundered through six different virtual currency accounts to facilitate “pig butchering” scams. The actors behind “pig butchering” develop relationships with victims, eventually convincing them to invest in fraudulent cryptocurrency platforms, leading to victims being unable to access the funds they invest. U.S. Department of Justice
U.S. Government Charges Estonian National for Using Front Companies to Evade Sanctions to Purchase U.S.-Made Electronics and Penetration Testing Software, the attempted purchases were to support the Russian-government. Andrey, Shevlyakov of Estonia, was sanctioned by the U.S. in 2012 for attempting to purchase technology for Russia’s military and government. Shevlyakov was charged with trying to purchase equipment to support electronic warfare systems which cannot be sold to entities in Russia, and Shevlyakov also attempted in 2020 to purchase a license to Metasploit Pro, which is considered a dual-use technology. U.S. Department of Justice
Ukrainian Law Enforcement Arrest Cyber Actors Responsible for $ 4.3 million in Fraud Targeting Users Throughout Europe, the actors created over 100 phishing sites that sold goods at very low prices, and the cyber actors would steal victim credit card data from the transactions. The stolen credit card information was then used to purchase goods which were then resold and laundered the proceeds through a network of money mules. Bleeping Computer
Cyber Vulnerabilities
New Ransomware Variant, Rorschach, One of Fastest Encrypting Ransomware Variants, no cyber actor has claimed responsibility for the Rorschach variant, but it has similarities to the Babuk variant and to LockBit 2.0 and can encrypt 220,000 files in four and half minutes, compared to LockBit 3.0, which needs seven minutes. Rorschach utilizes DLL side-loading to load the ransomware payload and exploits Palo Alto’s Cortex XDR Dump Service Tool to deliver the malicious dll file. Attacks on Rorschach have been identified throughout Europe, Asia, and the Middle East. The Hacker News
Technology Engineers at Samsung Accidentally Shared Sensitive Data with ChatGPT, Resulting in Company Limits to the Use of ChatGPT, multiple employees posted source code into ChatGPT in an effort to get ChatGPT to improve the code, and another posted internal meeting notes into ChatGPT. The incidents occurred after Samsung had lifted internal limits on the use of ChaptGPT and forced Samsung to introduce new limits to the use of ChatGPT for Samsung projects. Dark Reading
Tax-Related Phishing Scheme by Cyber Group Tactical#Octopus Used to Distribute Malware, the actors send emails with password-protected zip files which contain a shortcut file leading to a malicious file downloaded to a victim’s computer, allowing access to a victims system. Once the Tactical#Octopus actors have access to victim systems they are able to track keystrokes and capture clipboard data. The Record
Cyber-Actors Sell Malicious Access to Google Play Developer Accounts and Malicious Android Apps, With Prices as High as $20,000, according to research reviewing Dark Web activity between 2019 and 2023. Some developer accounts sold for as low as $60 while the source code for a loader allowing a user to develop multiple malicious apps and modify code was offered for sale for as high as $20,000. Dark Reading
Apple Releases Updates to Address Zero-Day Vulnerabilities Being Exploited, two new vulnerabilities, CVE-2023-28205 and CVE-2023-28206 were announced by Apple, along with security updates to address the zero-day vulnerabilities. The CVE’s impact Apple’s iPhone, iPad, and Mac operating systems as well as the Safari web browser and are currently being exploited by unknown cyber actors. The Hacker News
Geopolitical News
Finland Officially Joins the NATO Military Alliance, Finland, which previously has pursued neutrality since World War II, pursued NATO membership following Russia’s invasion of Ukraine in 2022. Finland’s membership increases the number of NATO countries bordering Russia, who has warned it will take “retaliatory measures” for what it claims to be security threats with the addition of Finland to NATO. The website for Finland’s Parliament suffered a denial-of-service attack by a pro-Russian cyber group, who claimed it was in response to Finland’s NATO membership. AP News
U.S. Intelligence Leak Regarding War in Ukraine Challenging Relationship with International Allies, in early March over 100 classified intelligence documents were posted to a Discord server regarding the war in Ukraine. The leak of the documents has caused international allies to question how the leak happened and its impact on future intelligence sharing between the U.S. and allied countries. Politico
Japan, South Korea and US Leaders Call for Increased International Cooperation on Enforcing U.N. Ban on Use of North Korean Workers in Foreign Countries, as of 2019 North Korea had approximately 100,000 individuals worldwide working in multiple industries to generate revenue used to support North Korean weapons programs. Despite UN sanctions, North Korea actively pursues a weapons development program focused on long range and nuclear missiles and has threatened to enhance its own military capabilities if the U.S., Japan and South Korea worked together to increase security cooperation. AP News
U.S. Announces $25 Million in Cybersecurity Aid to Government of Costa Rica, the funding will support Costa Rica following two significant ransomware attacks in 2022. In April 2022, Costa Rica was the victim of the Conti ransomware group and in May, was the victim of the HIVE ransomware group. Conti which declared its support for the Russian government following the invasion of Ukraine, may have been retailing against Costa Rica’s pro-Ukrainian stance according to Costa Rica’s president. CyberScoop
United Kingdom Government Supports ‘Accountable’ Operations Conducted by National Cyber Force, the joint intelligence and military cyber force was established in 2020 to support the consolidation of the U.K.’s offensive cyber operations. The U.K. promoted its daily offensive cyber activities as ‘accountable, precise, and calibrated’ in contrast to the cyber activities of Russia and China, and hopes other governments will work together to establish shared values on the use of offensive cyber operations in the future. The Record
Content from this threat briefing was provided by Nelnet’s CyberSecurity Threat Intel.
Sign Up
To receive Threat Briefings by email.

