
With the release date for the latest version of the Payment Card Industry Data Security Standard (PCI DSS), version 4.0, recently shifted back to Q4 of 2021, many in the industry are anxiously awaiting the publication and making predictions on expected changes.
The release of v4.0 was initially planned for Q2 of 2021, however, after the initial drafts and request for comment (RFC) periods, the Security Standards Council (SSC) decided to allow for additional feedback on supporting documents like the Self-Assessment Questionnaires (SAQs).
The PCI SSC is continually reviewing the payment card industry, assessing how organizations are handling cardholder information, researching new trends in payment technologies, and evaluating new and evolving risks and threats. The SSC analyzes recent data breaches and reviews how these incidents could have potentially been prevented. Their mission is, and has always been, protecting cardholder information the new version will build on the maturity of the existing DSS and modify it to better fit today’s threat landscape. The SSC has stated that the priorities for PCI DSS v4.0 include a focus on the overall security objectives and adding flexibility.
The 12 core requirements should remain fundamentally the same, but many of the requirements will now be written as outcome-based statements focused on implementation of the security control as the end result. Wording might simply change from what must be implemented to what the resulting outcome should be. Intent statements are also being added to help clarify what needs to be achieved, with more flexibility as to how an organization achieves that outcome.
Along these lines, one of the most significant changes is a new, customized validation approach that will replace the current compensating control. With PCI DSS v4.0, organizations will be able to confirm that they perform a control as outlined in the requirement, or they can opt for a customized implementation in which they show that the intent of the requirement is being met. As an example, if we look at the current password requirements in PCI DSS v3.2.1, some of the controls like 7 characters, 90 day reset, etc. are slightly outdated compared to current industry recommendations. Security best practices include recommendations for longer passphrases, and with that, the password reset timeframe has been extended. With the customized validation approach, an organization will be able to outline their strategies and controls for strong passwords. This will allow organizations more flexibility in how they secure their environments.
The new standard will tighten down on controls and reinforce security as a continuous, business-as-usual process. There will likely be changes to SAQ eligibility and predictions for changes to the SAQ requirements include:
- Revisions to requirements around passwords and authentication methods to accommodate different options and align more closely with the NIST MFA/password guidance (NIST SP 800-63).
- Broader applicability and the inclusion of widely accepted best practices for encrypting cardholder data on trusted networks. With cyber threats becoming more prevalent, especially within ecommerce environments, the need to keep cardholder data secure during transmission is critical.
- Monitoring requirements to account for recent advancements in technology, including next generation network and endpoint detection tools. Requirements will also be more accommodating for services like cloud hosting, which we see more and more merchants moving towards. SAQ A may see additional requirements or changes applicable to web re-direction servers due to the increased attacks on ecommerce environments.
- New requirements asking organizations to verify their PCI DSS scope, and ensure accuracy and completeness of their cardholder data environment (CDE).
- Updates to the annual risk assessment requirement to provide greater clarity and guidance, and help organizations come out of their assessments with a more useful risk analysis.
- Additions to security awareness training requirements for end users to include best practices for preventing phishing and social engineering.
- Additional requirements for service providers (how you monitor them and what responsibilities should be defined within contracts).
One area that many in the industry would like addressed in v4.0 is Voice over Internet Protocol (VoIP), however, recent drafts have not shown any additional emphasis on VoIP traffic. In November 2018, the PCI SSC provided a supplemental guidance document for telephone-based payments that reinforced VoIP networks are considered in scope just as regular IP-based networks. However, many organizations are struggling to implement secure and compliant VoIP networks. Fortunately, technologies for securing and encrypting voice traffic are improving, and there are solutions to help reduce or limit the scope of your VoIP network. We won’t know until the final version is released if the SSC will provide any more specific guidance regarding VoIP traffic.
Is there anything organizations can do now to prepare? For now, just continue to ensure your merchants are compliant with version 3.2.1 and shore up any areas of non-compliance. The SSC has clearly stated that you should not make any changes related to v4.0 until the final version is released and the final requirements are defined. Fortunately, there will be an overlapping sunset date, and organizations will not be required to be compliant with v4.0 immediately upon its release. Both versions will be active through the end of 2023, and merchants will be able to attest with 3.2.1 or 4.0 in 2022 and even 2023. These future dates are not yet known since the Standard is still under development, but organizations should not anticipate the retirement of v3.2.1 until two years after the publication of v4.0. There will also be future-dated requirements within the new standard that will not require compliance until an even later date.
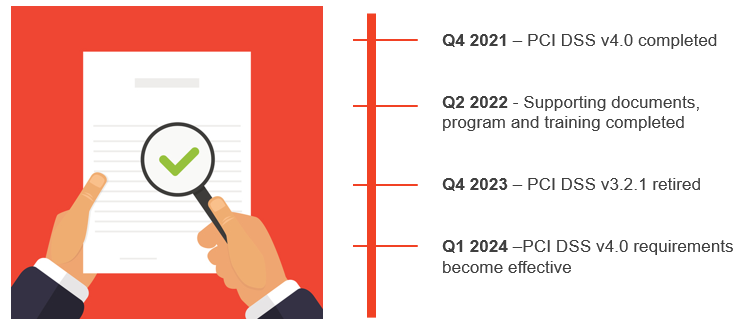
This timeline should allow for a smooth transition between versions and provide merchants with adequate time to develop new processes, implement controls, etc. before the new requirements are enforced.
CampusGuard will continue to evaluate any information regarding PCI DSS v4.0 and will communicate any updated information or details to your teams as applicable. Please contact us with any questions.
Some additional guidance from the CampusGuard Security Advisor Team:
[Ko]: The PCI DSS version 4.0 is being marketed as a “brand new PCI DSS” but the reality is that this is an update to an already mature and stable standard. The best course of action for preparing for the release of PCI DSS 4.0 is to continue to be compliant with the PCI DSS version 3.2.1. As the PCI DSS v4.0 is still in a draft state, it is not advised to make any changes to your environments using non-finalized guidance. As stated, there will be a long overlap while both the current standard and new standard are supported, with ample time to plan for and make changes to your environments.
We are anticipating the release of draft self-assessment questionnaires (SAQs) in the coming months. For those that are SAQ eligible, we’ll need to continue to wait for finalized versions of SAQs to see which new or changed requirements will be applicable to each SAQ.

