Preventing Ransomware By the Numbers
$265 Billion+
Predicted global ransomware damage costs by 2031
– Cybersecurity Ventures
Every 2 seconds
The predicted frequency of ransomware attacks will occur by 2031.
– Cybersecurity Ventures
$1.82 Million
Estimated cost to recover from a ransomware attack in 2023
-Sophos Report
45%
Of organizations that used backups recovered their data within a week
-Sophos Report
79%
Of higher ed institutions experienced a ransomware attack
-Sophos Report
Leading Cause of Ransomware Attacks
An exploited vulnerability was the leading cause of ransomware attacks, at 36%, followed by compromised credentials, at 29%, and emails, at 31%.
-Sophos Report
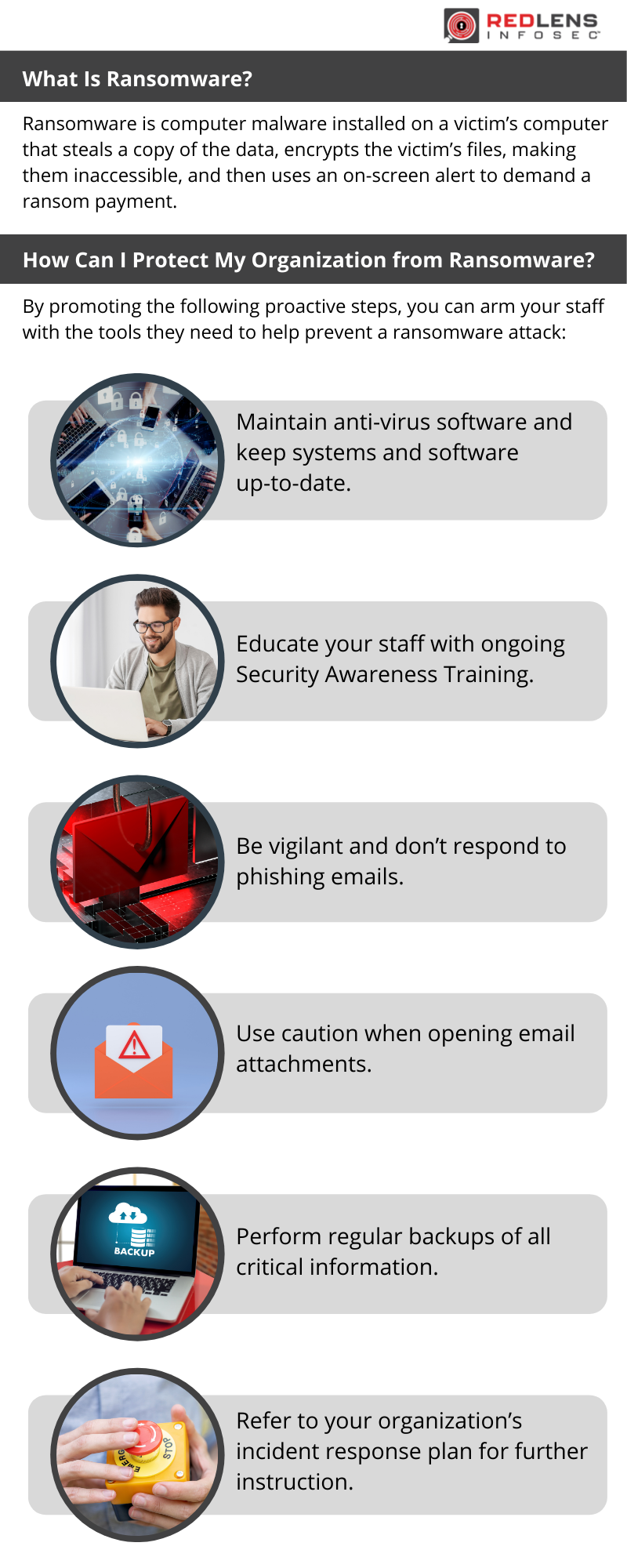
What Is Ransomware?
Ransomware is computer malware installed on a victim’s computer that steals a copy of the data, encrypts the victim’s files, making them inaccessible, and then uses an on-screen alert to demand a ransom payment.
How Can I Protect My Organization from Ransomware?
- By promoting the following proactive steps, you can arm your staff with the tools they need to help prevent a ransomware attack:
- Maintain anti-virus software and keep systems and software up-to-date.
- Educate your staff with ongoing Security Awareness Training.
- Be vigilant and don’t respond to phishing emails.
- Use caution when opening email attachments.
- Perform regular backups of all critical information.
- Refer to your organization’s incident response plan for further instruction.
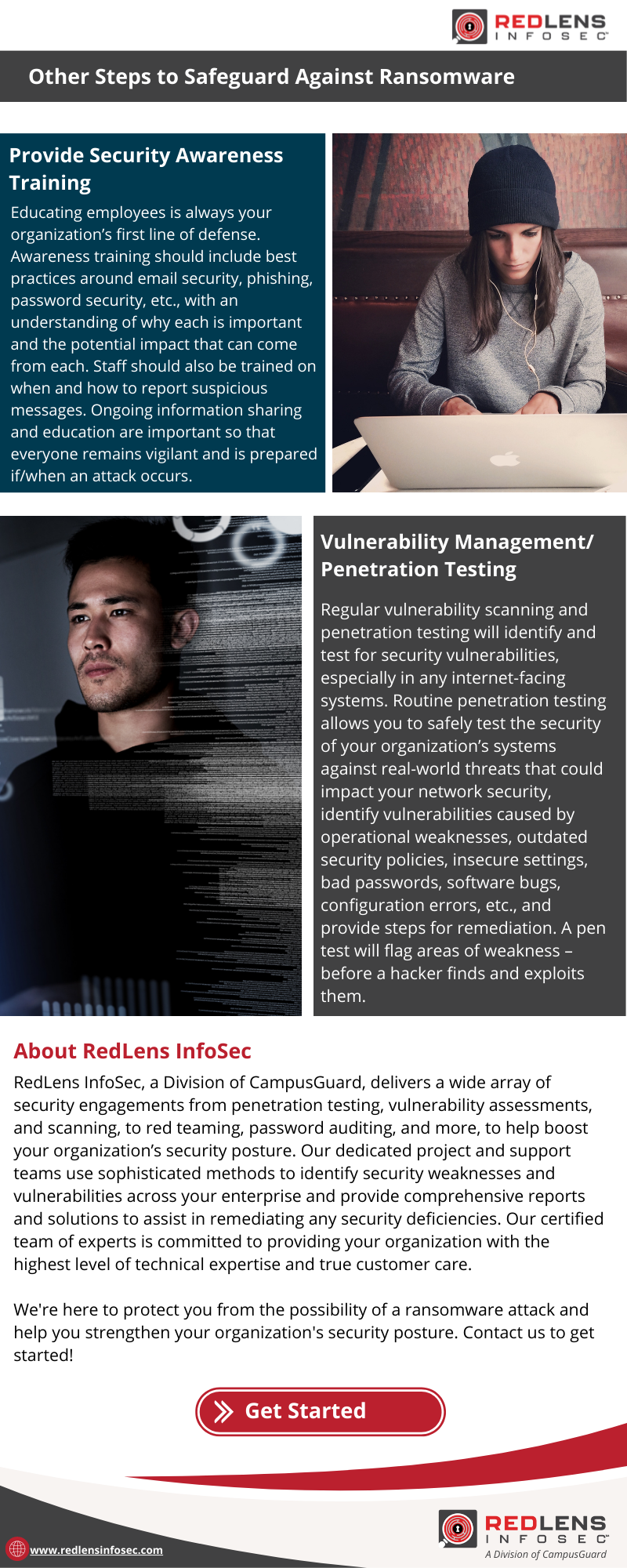
Other Steps to Safeguard Against Ransomware
Your organization can dedicate security efforts and resources to proactively identify exploitable vulnerabilities and the early signs of an attack and deploy preventative measures and technologies.
- Prioritize identifying and patching software vulnerabilities
Verify that all of your operating systems, applications, and software are up to date. Establish a defined process that ensures systems are updated regularly and the latest patches are installed automatically. - Monitor network traffic for suspicious activity
A Splunk report revealed a typical ransomware incident takes only 42 minutes to complete, making it almost impossible to stay in front of it if you aren’t alerted to the suspicious activity until after your systems have been compromised. Proactively detecting and responding to a potential attack is critical to minimizing the overall impact. - Regularly test your backup and disaster recovery/ incident response processes
Test your backup processes and ensure you will be able to restore systems and data if needed. Your organization should also prepare for and facilitate a tabletop exercise to ensure that everyone knows their individual responsibilities and who to contact during a cybersecurity incident. - Conduct routine risk/security assessments
Performing routine security and risk assessments can help inform your organization of identified risk levels and develop risk-tolerance and response plans. This can also help your organization identify the highest priority action items to decrease overall risk, and provide senior leaders, auditors, Boards, and regulators with a high-level overview of the organization’s cyber resilience and areas in need of improvement.
- Provide Security Awareness Training
Educating employees is always your organization’s first line of defense. Awareness training should include best practices around email security, phishing, password security, etc., with an understanding of why each is important and the potential impact that can come from each. Staff should also be trained on when and how to report suspicious messages. Ongoing information sharing and education are important so that everyone remains vigilant and is prepared if/when an attack occurs. - Vulnerability Management/ Penetration Testing
Regular vulnerability scanning and penetration testing will identify and test for security vulnerabilities, especially in any internet-facing systems. Routine penetration testing allows you to safely test the security of your organization’s systems against real-world threats that could impact your network security, identify vulnerabilities caused by operational weaknesses, outdated security policies, insecure settings, bad passwords, software bugs, configuration errors, etc., and provide steps for remediation. A pen test will flag areas of weakness – before a hacker finds and exploits them.
About RedLens InfoSec
RedLens InfoSec, a Division of CampusGuard, delivers a wide array of security engagements from penetration testing, vulnerability assessments, and scanning, to red teaming, password auditing, and more, to help boost your organization’s security posture. Our dedicated project and support teams use sophisticated methods to identify security weaknesses and vulnerabilities across your enterprise and provide comprehensive reports and solutions to assist in remediating any security deficiencies. Our certified team of experts is committed to providing your organization with the highest level of technical expertise and true customer care.
We’re here to protect you from the possibility of a ransomware attack and help you strengthen your organization’s security posture. Contact us to get started!